In today’s digital age, where most business is conducted online, reputation management is vital for any organization. However, with the rise of the internet and social media, it has become easier for malicious actors to launch reputation attacks, which can harm a company’s reputation and bottom line.
Here, we will explore some common reputation attack scenarios and provide strategies for defending against them. From fake reviews to online harassment, we will discuss the tactics that attackers use and the steps companies can take to protect their online reputation. So, whether you’re a small business owner or a large corporation, it’s important to stay vigilant in the face of potential reputation attacks.
Importance of Reputation Management to Defend Against Online Reputation Attacks

Reputation is like a first impression. It’s hard to shake off and even harder to rebuild. Managing your online reputation is crucial in the digital age, where information travels quickly and the internet never forgets. Think of it like an online game of Jenga; one wrong move and your reputation comes tumbling down. But with the right strategy and defense mechanisms, you can protect your online reputation from digital reputation attacks and keep your Jenga tower standing tall.
Different Types of Reputation Attacks

Online reputation attacks are a constant threat in today’s digital age. They come in many forms, but some of the most common include fake reviews, online harassment, smear campaigns, and social engineering. These attacks are designed to damage a business’s reputation and can have serious consequences. But don’t worry; with the right strategy and staying vigilant, you can protect your online reputation and keep your business thriving. Don’t let the bad actors win. Take control of your online presence and secure your reputation today!
Common Reputation Attacks
Reputation management is vital for any organization in today’s digital age. However, with the internet and social media, it has become easier for malicious people to launch cyber reputation attacks that can harm a company’s reputation and bottom line. We will explore some common reputation attack scenarios and provide strategies for defending against them. From fake reviews to online harassment, we will discuss the tactics that attackers use and the steps companies can take to protect their online reputation.
Fake Reviews

Fake reviews, oh, the bane of a business’s existence. These devious little things are created by malicious people who want nothing more than to damage a business’s reputation. But how exactly do they do it?
Well, it’s not as complicated as you might think. Sometimes, attackers create fake accounts and write fake positive or negative reviews to skew a business’s rating. They can also use automated bots to generate a large number of fake reviews in a short period. And if that wasn’t enough, they could also pay people or even use paid services to write fake reviews on behalf of a business.
It’s a sneaky and underhanded tactic, but unfortunately, it’s also effective. Fake reviews can harm a business’s reputation and drive away potential customers. But don’t despair. With the right tools, you can spot and report fake reviews and take action to protect your business from these digital reputation attacks
The Impact of Fake Reviews on a Business
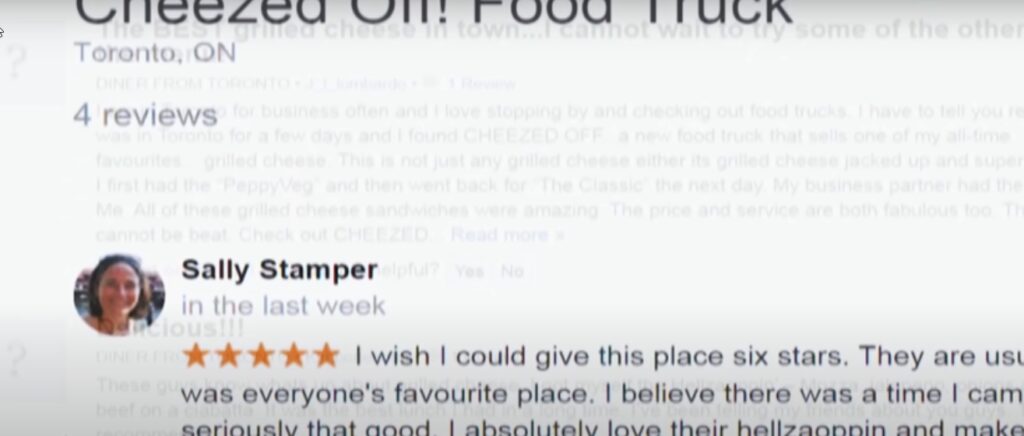
Fake reviews can have a devastating impact on a business’s reputation and bottom line. These online reputation attacks can skew a business’s rating and give potential customers a false impression of the offered service or product.
Imagine you’re looking for a new restaurant to try, and you come across one with an excellent rating, but when you get there, the food is terrible, and the service is even worse. You’ll be disappointed, and you’ll likely tell your friends and family about your bad experience. Now imagine that the restaurant’s high rating was due to fake reviews. The restaurant just lost more than just your business. It lost the potential business of everyone you told.
Fake reviews can also make it difficult for businesses to compete with their rivals. Attackers can give their companies an unfair advantage by creating fake positive reviews for their own business and negative reviews for their competitors.
Online Harassment

Online harassment is the virtual version of a playground bully. It’s a tactic malicious people use to target a business or individual with negative comments and messages on social media or other online platforms.
These cyber reputation attacks can take many forms, from nasty comments on your business’s social media accounts to personal attacks on the business owner or employees. It can also include creating fake accounts to harass and intimidate.
It’s not just unpleasant. It can also be damaging. Negative comments and reviews can harm a business’s reputation and discourage potential customers. This factor contributes to a hostile work environment and makes it difficult for employees to do their job.
But just like playground bullies, online harassers thrive on attention. The more you engage with them, the more they’ll continue their behavior. The best way to deal with online harassment is to have a plan and not engage with the harasser.
It’s important to remember that online harassment is not just a nuisance. This reputation attack is a serious issue that can harm a business’s reputation and bottom line.
Types of Online Harassment
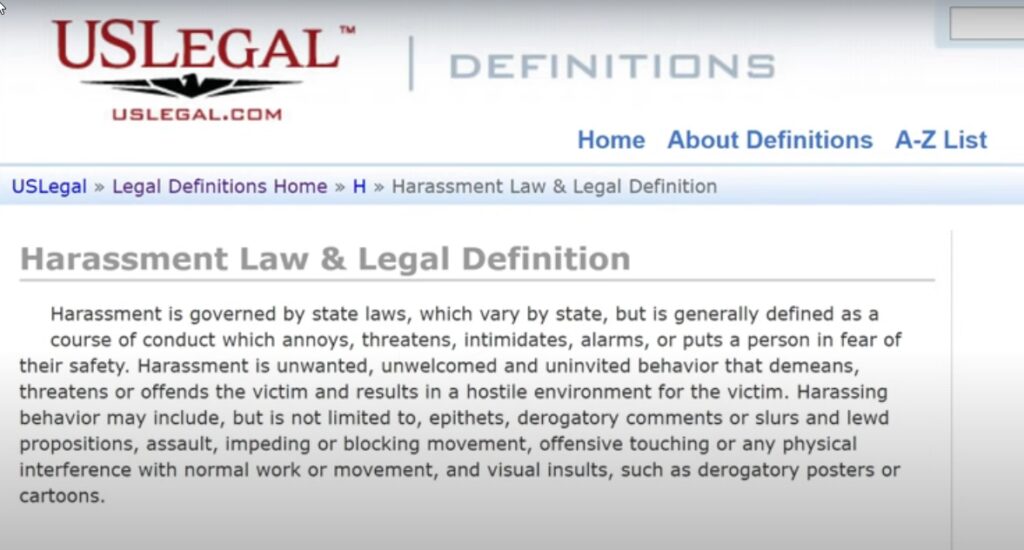
Online harassment comes in many forms, it can be subtle, or it can be outright vicious. Here are the different types of online reputation attacks.
- Trolling- An act of someone making damaging, off-topic, or offensive comments with the primary intent of provoking a reaction from other users
- Cyberbullying- This is when someone uses the internet to harass, threaten or humiliate another person repeatedly
- Doxxing- When someone publicly releases an individual’s personal information without consent, such as their address, phone number, or email.
- Impersonation: This is when someone creates a fake account to impersonate another person or business to harm their reputation.
These are just a few examples, but it’s important to remember that attackers constantly develop new ways to harass and harm others online. It’s crucial to stay vigilant and plan to deal with online harassment.
The Impact of Online Harassment on a Business

Online harassment can severely impact a business’s reputation and bottom line. It can discourage potential customers and create a negative image of the company. Imagine if a potential customer comes across a business’s social media account filled with negative comments and personal attacks, they’re likely to think twice before doing business with that company.
It propagates hostility in your work environment, making it difficult for employees to do their job. Imagine if an employee constantly receives personal attacks or threatening messages, it will be hard for them to focus on their work, and it could even affect their mental well-being.
It can also lead to legal issues. For example, if an employee or a business is being harassed and threatened, they may need to involve the authorities. They could also look for their legal options.
Moreover, online harassment or cyberbullying can take a toll on the personal life of the person or the business owner. It’s not just a nuisance. It’s a serious issue that can harm a business. It creates a hostile work environment, affects employees’ mental well-being, and even leads to legal problems. This is crucial to stay vigilant and take action to protect your online presence and reputation.
Smear Campaigns

Smear campaigns, the virtual version of a whispering campaign, are used by malicious individuals to spread false or misleading information about a business or individual to damage their reputation.
It can take many forms, from spreading rumors about a business or its owners to creating fake news articles or social media posts. The attackers can use various platforms to distribute the information, such as social media, news websites, forums, and even traditional media.
One common tactic used in smear campaigns is creating fake accounts to spread false information. They can also use bots to amplify the reach of their message and make it more believable.
It’s a sneaky and underhanded cyber reputation attacks, but it can be devastatingly effective. Smear campaigns can harm a business’s reputation and drive away potential customers. It also makes the work of your employees extra tricky.
The Impact of Smear Campaigns on a Business

Smear campaigns can have a devastating impact on a business. By spreading false or misleading information, attackers can create a negative image of the company and discourage potential customers from doing business with them.
Imagine if a potential customer comes across false information about a business. It could make them think twice about doing business with that company. For example, if a smear campaign spreads incorrect information that a restaurant serves undercooked food, it’s likely to discourage customers from eating there.
Employees might be affected by these reputation attacks, making it difficult to do their job. In some cases, it may even affect their mental well-being.
Furthermore, smear campaigns can also give rival businesses an unfair advantage. By spreading false information about a company, attackers can create a negative image and discourage potential customers, leading to a decrease in revenue for the targeted business.
Social Engineering

Social engineering, the art of manipulation, is a tactic used by malicious people to trick individuals into divulging sensitive information that can be used to damage their reputations.
It’s unlike in the movies where the attackers wear black hoodies and type furiously on a computer. It’s much more subtle and sophisticated. Here are the different kinds of social engineering attacks:
- Phishing- An attacker sends an email or message pretending to be a trustworthy source, such as a bank or a government agency, and tricks the recipient into providing personal information or clicking on a malicious link
- Vishing- An act when an attacker uses a phone call to trick an individual into giving personal information
- Pretexting- These reputation attacks create a fake identity and use it to gain an individual’s trust to obtain sensitive information.
- Baiting- This is when an attacker tempts an individual with something they want, such as a free gift or a job offer, to obtain sensitive information.
The Impact of Social Engineering on a Business
Social engineering reputation attacks can significantly impact a business’s reputation and bottom line. By tricking individuals into divulging sensitive information, attackers can access a business’s confidential data and use it to harm its reputation. For example, an attacker may use a phishing email to trick an employee into providing their login credentials, which can then be used to access the company’s financial records.
It can also lead to financial losses, as attackers can use the sensitive information obtained through social engineering to conduct fraudulent activities such as making unauthorized transactions or stealing money.
Moreover, social engineering attacks can create a terrible work environment and make it difficult for employees to do their job. For example, suppose an employee falls for a phishing email, and the attacker gains access to the company’s confidential information. In that case, it can create a sense of mistrust and insecurity among the employees. This may also cause anxiety and stress.
Defending Against Reputation Attacks

Protecting your online reputation is crucial in today’s digital age. Reputation attacks come in many forms and can harm a business in countless ways. But with the right strategies, you can defend against these attacks and protect your online reputation.
This section will discuss different techniques and tools businesses can use to monitor their online presence, respond to negative reviews or comments, implement security measures, and build a positive reputation. You can protect your business from reputation attacks and keep your online presence strong by staying vigilant and taking action.
Monitoring Your Online Presence

Monitoring your online presence is like having a virtual lookout. It allows you to monitor what’s being said about your business and avoid any potential digital reputation attacks. It’s like having a bird’s eye view of your online reputation. You can spot potential issues and take action before they become a problem.
- Setting up Google Alerts – One way to monitor your online presence is by setting up Google Alerts. Google Alerts is a free service that sends you an email notification when your business is mentioned online. It’s like having a virtual assistant that keeps an eye on your online reputation and alerts you when something important pops up.’
- Regularly checking social media accounts- Social media is a powerful tool. It allows you to engage with your customers and build a positive reputation. But it also allows others to leave comments and reviews, which can be both good and bad. Regularly checking your social media accounts will enable you to respond to negative comments or reviews and address potential issues before they become a problem.
Responding to Negative Reviews or Comments
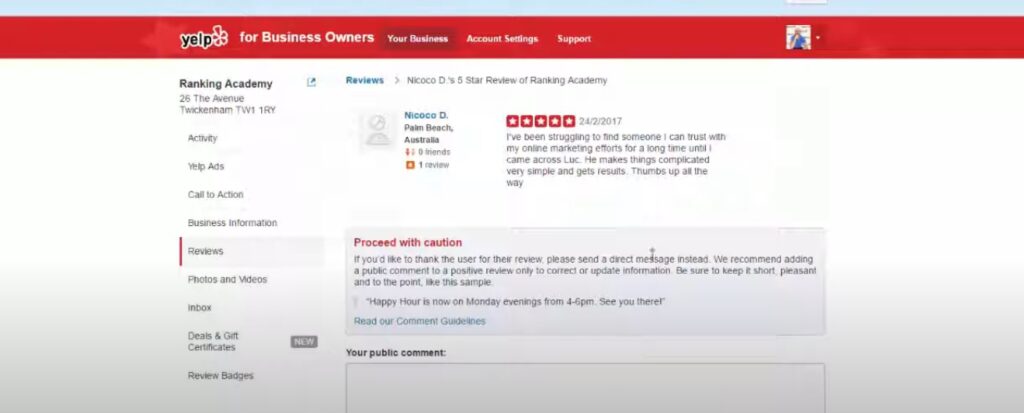
Responding to negative reviews or comments is another crucial aspect of protecting your business from online reputation attacks. It helps you mitigate the effect of negative comments before they even lead to a crisis.
Addressing Customer Complaints
When responding to negative reviews or comments, it’s important to address customer complaints promptly and professionally. This shows that you care about your customers and are willing to take action to resolve any issues they may have. By addressing customer complaints, you can not only fix the problem at hand but also build trust and improve your reputation.
Disputing False Reviews
Another critical aspect of responding to negative reviews or comments is disputing false reviews. False reviews can damage a business’s reputation and discourage potential customers. By discussing false reviews, you can take action to have them removed and protect your online reputation.
Implementing Security Measures

Monitoring your online presence and responding to negative reviews or comments are essential to defend against reputation attacks. Still, it’s not just about what you do after the attack happens. It’s also about taking preventative measures to protect your business from future attacks. One action is implementing security measures.
Two-Factor Authentication
Regarding security measures, one of the most effective ways to protect your business is by enabling two-factor authentication. Two-factor authentication is like an extra layer of protection by requiring a second verification form, such as a fingerprint or a code sent to your phone and a password. With this, it is more difficult for attackers to gain access to your accounts and steal sensitive information.
Strong Passwords
Another critical security measure against reputation attacks is using strong passwords. Strong passwords are harder to guess and more complicated to crack. They can be a combination of letters, numbers, and special characters. Avoid using personal information or guessable words as passwords.
Building a Positive Reputation

By providing excellent customer service and building a solid brand, you can create a positive image of your business and attract more customers.
Providing Excellent Customer Service
Building a positive reputation starts with providing excellent customer service. When your customers are happy, they’re more likely to leave positive reviews and recommend your business to others. You can improve your reputation, increase customer loyalty, and drive more business by providing excellent customer service.
Building a Strong Brand
Another critical aspect of building a positive reputation and protecting yourself from reputation attacks is building a solid brand. A strong brand can help your business stand out in a crowded market and create a positive image in the minds of potential customers. Establishing a strong brand that communicates your business’s value and unique characteristics is essential. You must consistently reinforce that message across all your marketing and communication channels.
Conclusion

Protecting your online reputation is crucial in today’s digital age. Reputation attacks come in many forms and can harm a business’s reputation and bottom line. But with the right strategies, you can defend against these attacks and protect your online reputation.
Monitoring your online presence, responding to negative reviews or comments, implementing security measures, and building a positive reputation are all essential to defending against reputation attacks. It’s important to stay vigilant and take action to protect your online presence and reputation. By staying on top of your online presence and taking proactive measures, you can protect your business from attacks and keep your online reputation strong.
Tags: crisis management, reputation management